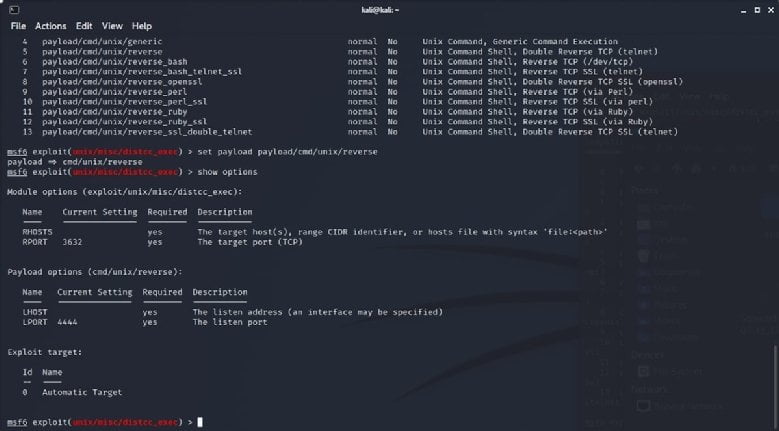
Students in my Penetration Testing course, CIS4200, are constantly tasked with reverse engineering, replicating, or defending against modern security vulnerabilities. At the beginning of each module they are assigned a lab-based walkthrough that introduces new concepts, reinforces old concepts, and eliminates homework boredom. Then they are slowly guided deeper into each tool and skillset before finally being asked to demo what they have learned and capture a hidden flag. This type of incremental reinforced learning is widely prevalent in our sector, and the Capture the Flag (CTF) scenarios my students face are on par with those the top training agencies utilize and are all based on real world vulnerabilities and attacks.
This course is currently offered both as a for-credit college course and as a private instructor-led teaching.
ISM4324: Computer Forensic Analysis
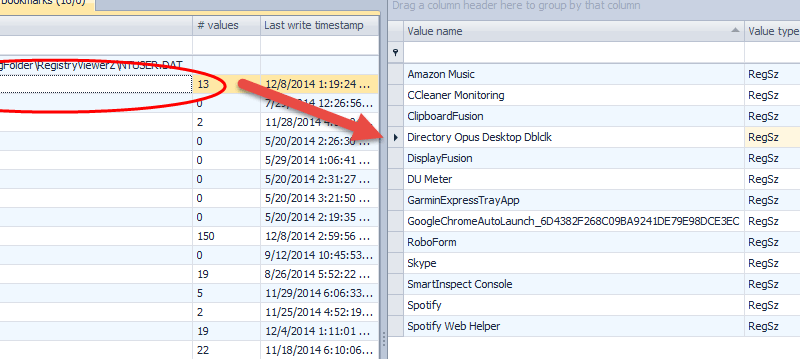
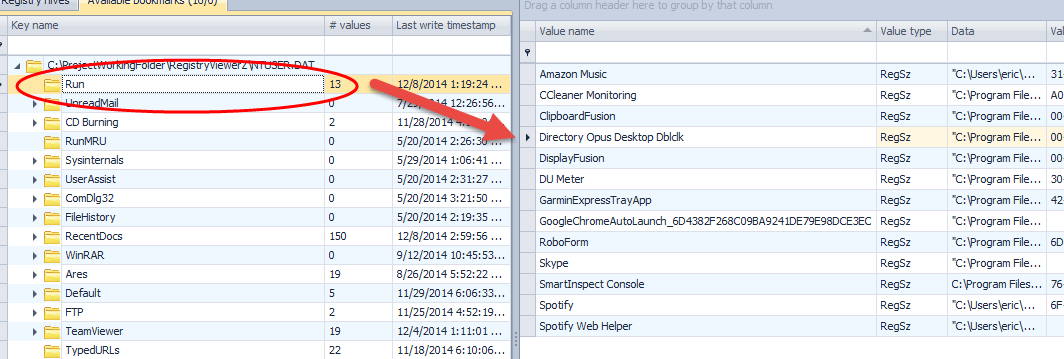
This course focuses on the techniques and methods used to conduct forensic examinations of digital evidence. The course covers the entire process of computer forensics, from the initial seizure and preservation of evidence, to the analysis and presentation of findings in a court of law.
One of the main topics covered in the course is the use of forensic tools and software, such as EnCase and FTK, to recover and analyze data from various types of digital devices, including computers, smartphones, and storage media. Students will also learn about the legal and ethical considerations involved in computer forensics and the proper handling of evidence to ensure its admissibility in court.
The course also covers the various types of digital evidence that may be encountered in a forensic examination, including deleted files, hidden data, and encrypted files. Students will learn how to identify and extract relevant evidence and how to present their findings in a clear and concise manner.
In addition to the technical aspects of computer forensics, the course also covers the broader context of cybercrime and its impact on society. Students will learn about the different types of cybercrime, such as hacking, identity theft, and cyberstalking, and the legal and investigative challenges they pose.
This course is currently offered only as a for-credit college course.
ISM4320: Applications in Information Security
explores the practical applications of information security in different industries and organizations. The course covers a wide range of topics, including risk management, threat intelligence, incident response, and compliance.
One of the main focuses of the course is on the development of information security policies and procedures. Students will learn how to identify and assess security risks, and how to develop and implement effective security measures to mitigate those risks. The course also covers incident response planning and incident management, providing students with the knowledge and skills needed to respond effectively to security incidents.
Another important aspect of the course is the exploration of different types of cyber threats and vulnerabilities. Students will learn about the latest threats, including advanced persistent threats (APTs), and how to identify, assess, and defend against them. The course also covers compliance and regulatory requirements, providing students with an understanding of the legal and regulatory framework surrounding information security.
The course also provides hands-on experience through the use of various security tools, such as firewalls, intrusion detection systems, and vulnerability scanners. Students will have the opportunity to apply the concepts and techniques learned in class to real-world scenarios through lab exercises and projects.