This script will enumerate all AD servers in the specified domain and check them for critical event logs, inactive OUs, and outdated group policies. It is easy to run and will help harden your AD systems.
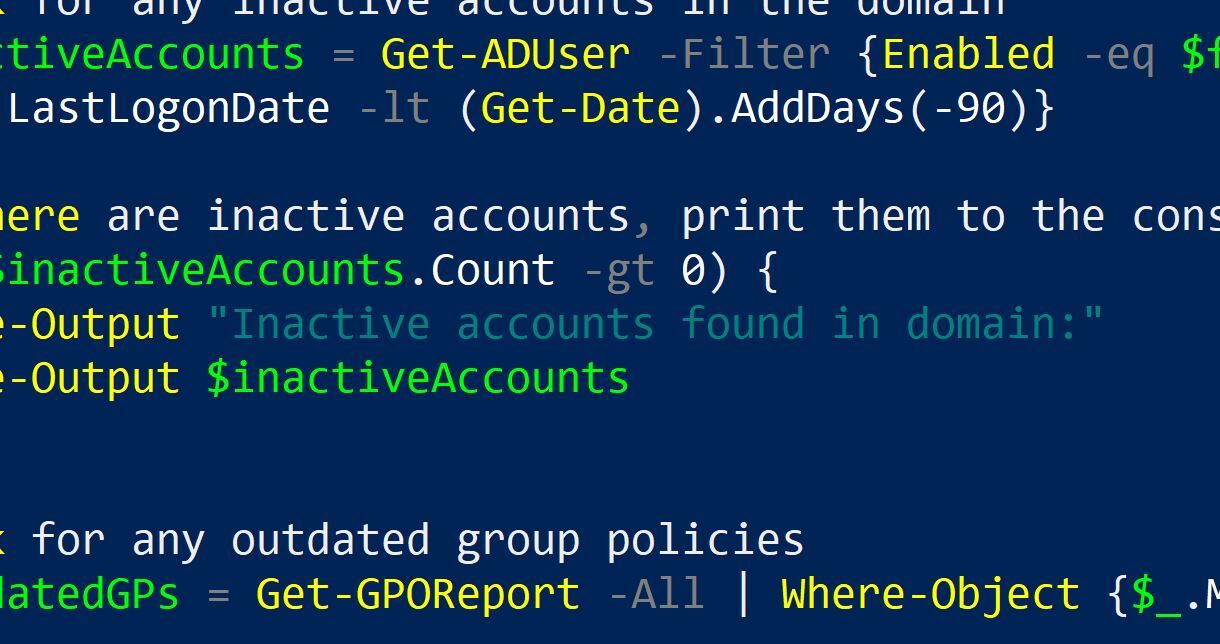
Set the domain to check $domain = "yourdomain.com"Get a list of all domain controllers in the domain$domainControllers = Get-ADDomainController -Filter * | Select-Object -ExpandProperty HostNameLoop through each domain controllerforeach ($dc in $domainControllers) {Check for errors in the event logs$errors = Get-EventLog -ComputerName $dc -LogName "Directory Service" -EntryType ErrorIf there are errors, print them to the consoleif ($errors.Count -gt 0) {Write-Output "Errors found on domain controller $dc:"Write-Output $errors}}Check for any inactive accounts in the domain$inactiveAccounts = Get-ADUser -Filter {Enabled -eq $false} -Properties LastLogonDate | Where-Object {$_.LastLogonDate -lt (Get-Date).AddDays(-90)}If there are inactive accounts, print them to the consoleif ($inactiveAccounts.Count -gt 0) {Write-Output "Inactive accounts found in domain:"Write-Output $inactiveAccounts}Check for any outdated group policies$outdatedGPs = Get-GPOReport -All | Where-Object {$_.ModificationTime -lt (Get-Date).AddDays(-30)}If there are outdated group policies, print them to the consoleif ($outdatedGPs.Count -gt 0) {Write-Output "Outdated group policies found in domain:"Write-Output $outdatedGPs}