In the field of cybersecurity, one of the most widely-used frameworks for describing the stages of a cyber attack is the Cyber Kill Chain. Developed by Lockheed Martin, this framework is a useful tool for understanding the various stages of an attack and the steps that organizations can take to defend against them.
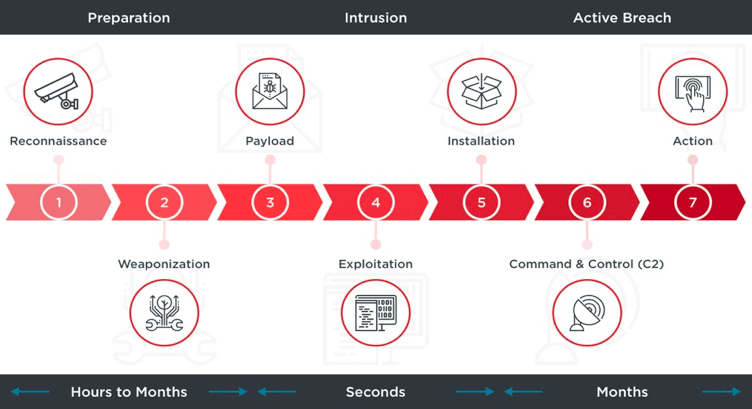
At a high level, the Cyber Kill Chain consists of seven stages:
- Reconnaissance: The attacker gathers information about the target and identifies potential vulnerabilities.
- Weaponization: The attacker creates a weapon (e.g., a malicious file or exploit) that can be used to exploit the identified vulnerabilities.
- Delivery: The attacker delivers the weapon to the target (e.g., via email or a compromised website).
- Exploitation: The attacker uses the weapon to exploit the identified vulnerability and gain access to the target’s systems.
- Installation: The attacker installs a persistent presence on the target’s systems to maintain access and control.
- Command and control: The attacker establishes a command and control infrastructure to remotely manage the compromised systems.
- Actions on objectives: The attacker achieves their intended goal, which could be data theft, destruction of data or systems, or some other malicious action.
Let’s take a closer look at each of these stages and how they can be defended against.
- Reconnaissance: In this stage, the attacker is gathering information about the target to identify potential vulnerabilities. This could involve scanning the target’s networks, searching for public-facing vulnerabilities, or even social engineering to gather information about the target’s employees. To defend against this stage, organizations can implement measures such as network segmentation, restricting access to sensitive information, and conducting regular security awareness training for employees.
- Weaponization: In this stage, the attacker creates a weapon that can be used to exploit the identified vulnerabilities. This could involve creating a malicious file, exploiting a software vulnerability, or even using social engineering to trick the target into executing the weapon. To defend against this stage, organizations can implement measures such as patching software vulnerabilities, deploying antivirus and antimalware solutions, and using email filtering to block malicious attachments.
- Delivery: In this stage, the attacker delivers the weapon to the target. This could involve sending a malicious email, compromising a website, or even using physical media (such as a USB drive) to deliver the weapon. To defend against this stage, organizations can implement measures such as email filtering, web application firewalls, and limiting the use of external media on corporate systems.
- Exploitation: In this stage, the attacker uses the weapon to exploit the identified vulnerability and gain access to the target’s systems. This could involve running code on the target’s system, bypassing authentication controls, or even using a privilege escalation exploit to gain administrative access. To defend against this stage, organizations can implement measures such as network segmentation, implementing strong authentication controls, and deploying intrusion detection and prevention systems.
- Installation: In this stage, the attacker installs a persistent presence on the target’s systems to maintain access and control. This could involve installing a backdoor, creating a new user account, or even modifying system files to ensure that the attacker can maintain access. To defend against this stage, organizations can implement measures such as deploying host-based intrusion detection and prevention systems, regularly monitoring system logs, and limiting the use of administrator accounts.
- Command and control: In this stage, the attacker establishes a command and control infrastructure to remotely manage the compromised systems. This could involve setting up a remote access tool, using a compromised server as a proxy, or even using social media platforms to communicate with the compromised systems. To defend against this stage, organizations can implement measures such as blocking outgoing traffic to known command and control servers, using intrusion detection and prevention systems, and regularly monitoring network traffic.
- Actions on objectives: In this final stage, the attacker achieves their intended goal, which could be data theft, destruction of data or systems, or some other malicious action. This could involve stealing sensitive data, encrypting critical systems, or using compromised systems to launch further attacks against other targets. To defend against this stage, organizations can implement measures such as deploying data loss prevention solutions, implementing strong access controls, and regularly conducting vulnerability assessments and penetration testing to identify and address vulnerabilities before they can be exploited by attackers.In conclusion, the Cyber Kill Chain is a useful framework for understanding the various stages of a cyber attack and the steps that organizations can take to defend against them. By implementing a comprehensive cybersecurity program that addresses each stage of the Cyber Kill Chain, organizations can significantly reduce their risk of a successful cyber attack. While there is no one-size-fits-all solution to cybersecurity, understanding the Cyber Kill Chain and implementing appropriate defenses can go a long way toward protecting organizations from the ever-evolving threat of cyber attacks.