Breaking Down the Cyber Kill Chain: Understanding and Defending Against Cyber Attacks
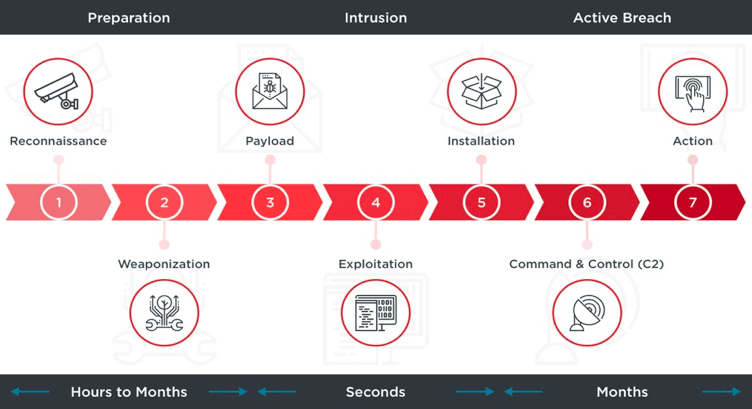
In the field of cybersecurity, one of the most widely-used frameworks for describing the stages of a cyber attack is the Cyber Kill Chain. Developed by Lockheed Martin, this framework is a useful tool for understanding the various stages of an attack and the steps that organizations can take to defend against them. At a […]
Python Tool: Quick Metadata, Stego, and Reverse GIS
A lightweight Python tool that accomplishes 3 objectives for the DFIR professional (scroll down for a more advanced explanation of each function): Extracts metadata from media files, and prints out any metadata that’s found Checks for steganography in both images and video frames Performs a reverse GIS on images Here’s a breakdown of how the […]
“The Dark Side of AI: How Chatbots like ChatGPT Threaten Information Security”
The rise of artificial intelligence (AI) has brought about many exciting advancements in technology, but it also poses a significant threat to the information security industry. One example of this is the use of AI-powered chatbots like ChatGPT. ChatGPT, as well as other similar chatbots, can mimic human communication so well that it can be […]
Securing the Vote: A Look at the Digital Election Security Measures Needed for the Upcoming POTUS Election
The integrity of our electoral process relies on the ability to trust that every vote is counted accurately, and that the outcome of the election reflects the will of the people. However, with the increased use of technology in the voting process, there are also increased opportunities for malicious actors to interfere.
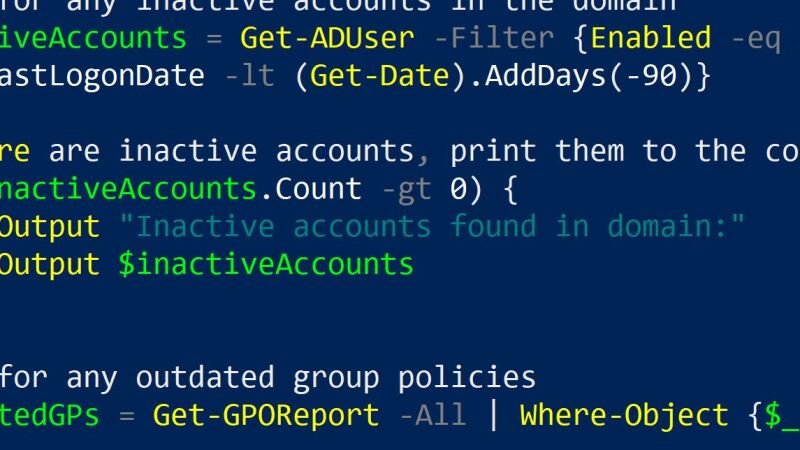
Simple Powershell Active Directory script to harden your servers
This script will enumerate all AD servers in the specified domain and check them for critical event logs, inactive OUs, and outdated group policies. It is easy to run and will help harden your AD systems. Set the domain to check $domain = “yourdomain.com” Get a list of all domain controllers in the domain $domainControllers […]
Challenges of Cloud Based Acquisition for DFIR Professionals
One aspect of digital forensics that has garnered significant attention in recent years is the use of cloud-based services for data storage and communication. While cloud computing offers numerous benefits, such as cost savings and increased accessibility, it also presents unique challenges for digital forensics investigators.